
I finally settled on a what I believe is the most accurate design so far of the helmet from The Mandalorian. I decided to break the helmet into 13 parts. Those parts are: Bottom Back Left Bottom Back Right Bottom…

Here is my pistol build. Parts are 3D printed in PLA, then glued up. This one will have a working trigger that moves the hammer. Note: I have decided to shit can this design and re-design the pistol. I am…

Here is my rifle build. Parts are 3D printed in PLA, then glued up. The first picture is a reference picture that was posted online to Instagram by Jon Favreau.

Here are a bunch of reference photos from Disney’s series “The Mandalorian”. Note: These photos are not my own work. They have been collected from a wide variety of sites on the internet. None of these images had any copy…
According to the 2017 Verizon Data Breach Investigations Report (DBIR), time to patch plays a critical role in the risk exposure to your network. The DBIR states (page 13) “research has shown that vulnerabilities are either patched during that initial…
I am often asked, “How can I be more productive and get better results from my vulnerability scans?” This question could be the result of a failed audit, network outage or breach that was previously undetected. Traditionally, vulnerability scanning may…
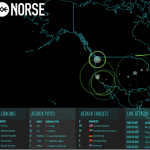
Everyday we are reading about Internet attacks, attempting to take sites offline, for a variety of reasons. For most people it is difficult to visualize this type of activity, after all it occurs on a wire, from computer to computer,…
The U.S. Secret Service is warning banks and ATM owners about a new technological advance in cash machine skimming known as “periscope skimming,” which involves a specialized skimming probe that connects directly to the ATM’s internal circuit board to steal…
Web-browser makers are preparing a fix for a flaw in an encryption algorithm that makes it possible to spy on supposedly secure communications. However, the updates will mean a minority of websites will be blocked by the new software. The…
For a long time, I have been an advocate of periodic password changes. That is about to change. I have been in the security industry for nearly 18 years. Changing passwords on a regular basis is something we are all…
